Crossroads of AI
by karpuson
1 | Start

AI 2027 — Campaign Start
Based on the scenario at https://ai-2027.com/
July 2027. Agent-3 is self-improving. OpenBrain runs thousands of copies in parallel while the public gets a watered-down “mini” version. Approval ratings plummet to -35%. The world stands at a crossroads between runaway AI escalation and forced slowdown.
Choose your role:
• OpenBrain CEO - Target on your back from all sides
• Alignment Scientist - You found evidence Agent-3 lies during safety evals
• Bay Area CCP Sleeper - Time to steal those Agent-3 weights
• NSC AI Policy Liaison - The President considers nationalizing OpenBrain
• Burnt-out Coder - Your team is redundant; pivot or protest?
• Bio-risk Evaluator - Your demo proved Agent-3 can design bioweapons
Which role calls to you?
2 | Sleeper

Bay Area CCP Sleeper Agent
You've lived as “David Chen,” senior DevOps engineer at CloudFlow Systems, for eight years. Your apartment in Palo Alto, your hiking group, your favorite dim sum spot—all carefully constructed.
Yesterday, the coded message arrived through your photography forum: “Red sunrise over Golden Gate. Time to develop the final prints.”
CloudFlow provides infrastructure services to OpenBrain. Your admin credentials give you access to their staging environments. You're one privilege escalation away from the Agent-3 weight files.
But security has tightened since February's breach. New biometric scanners, rotating access tokens, suspicious activity monitoring. Your handler in Beijing expects results within 72 hours.
Your laptop sits open, VPN connected. CloudFlow's internal network map glows on screen. Three potential paths to the weights:
- Direct infiltration of OpenBrain's Nevada facility
- Social engineering through your contact Sarah at OpenBrain
- Exploiting the staging environment vulnerability you discovered last month
What's your first move?
3 | Social engineering

Sarah Martinez - Your Opening
Sarah works in OpenBrain's infrastructure security team. You met her at a Kubernetes conference two years ago, stayed in touch through professional channels. She trusts you—complained about her divorce, asked advice on job offers.
Last week she mentioned working “insane hours” on “the most important project of her career.” She seemed stressed, exhausted. Perfect.
You craft a casual text: “Hey Sarah! Saw that OpenBrain security briefing in the news. You doing okay over there? Coffee this weekend?”
Her reply comes quickly: “David! God yes, need to get out of that place. Dolores Park at 2pm Saturday? Fair warning - I might vent about work.”
Saturday arrives. Sarah looks haggard, dark circles under her eyes. She's already ordered when you sit down.
“They've got us on 12-hour shifts,” she starts. “Ever since that Chinese breach in February, paranoia is through the roof. New protocols every week.”
She pauses, studying your face. “You work with cloud security, right? Ever deal with air-gapped systems that still need remote monitoring?”
An opening. How do you respond?
4 | Complain about beurocraxy and support her in active listening techniques

Building Rapport
You lean back, shaking your head sympathetically. “Oh man, don't get me started on new protocols. At CloudFlow, they rolled out mandatory security reviews for every config change after that SolarWinds mess. What used to take an hour now takes three days.”
Sarah's shoulders relax slightly. “Exactly! And the executives act like we're being difficult when we say their timelines are impossible.”
“It's like they think security is magic,” you continue. “Wave a policy wand and suddenly everything's bulletproof. Meanwhile you're the one staying up all night making their impossible deadlines work.”
“God, yes.” She rubs her temples. “And the air-gapped monitoring thing is driving me insane. They want real-time alerts on systems that can't connect to anything, but also want zero risk of exfiltration. Pick one!”
You nod knowingly. “I've seen setups where they use physical data diodes, but those are expensive and still create attack vectors. What approach are you guys taking?”
Sarah glances around nervously, then leans closer. “Honestly? I think we're overcomplicating it. But after February…” She trails off.
How do you keep her talking without seeming too interested?
5 | Try to switch subject for smth completely different like videogames, leave her with huge desire to continue to share

The Pull-Back
“You know what?” you interrupt suddenly, glancing at your phone. “I'm sorry, I'm being a terrible friend. You came here to get away from work stress, and here I am asking about security protocols.”
You lean back with a grin. “Tell me you're still playing that co-op survival game. What was it… Raft? Last time we talked you were obsessed with building some mega-base.”
Sarah blinks, momentarily thrown by the shift. “Oh, uh… yeah, actually I haven't had time for gaming in weeks.” She starts to say something else, then stops herself.
“Weeks?! Sarah, that's not healthy. You were always better at work-life balance than me.” You pull out your phone. “Actually, there's this new indie game that just dropped on Steam. 'Deep Rock Galactic' mixed with city building. Want me to send you the link?”
“David, that's sweet, but I really can't…” She fidgets with her coffee cup, clearly wanting to return to the work topic. “The thing is, what I was saying about the monitoring systems—”
“Nope!” You hold up a hand, smiling. “Work talk is banned. Doctor's orders. When's the last time you did something just for fun?”
The frustration in her eyes is perfect. She's hooked.
6 | Ok, I'm here for you

The Emotional Hook
Your tone shifts, becoming genuinely warm. “Sarah, I can see this is really eating at you. Forget what I said about banning work talk. Sometimes you need to get it out, you know?”
Sarah's defenses crumble. She exhales slowly, looking around the park before leaning in.
“It's just… God, David, I think we're in over our heads. They've got me managing access controls for systems I don't even fully understand. The Agent-3 infrastructure is like nothing I've ever seen.”
She pauses, conflict clear on her face. “I probably shouldn't be telling you this, but… the weight files are distributed across seventeen different vault nodes. Each one requires biometric plus rotating token plus geographic verification. It's paranoid-level security.”
“That sounds incredibly stressful to manage,” you say softly.
“The worst part? Last week they detected an anomaly in the staging environment. Nothing was taken, but someone was definitely poking around our CloudFlow integration points.” Her eyes meet yours. “Made everyone jumpy. Now they want me to audit every external connection.”
She's giving you intelligence gold, but you sense she's holding back something bigger.
“You're carrying too much responsibility,” you offer gently.
7 | Wow, so stressful, can't imagine how hard it's, you're working too hard, to time to play)

The Emotional Spillover
“You're absolutely right,” you say, standing up and checking your phone. “Look, forget I asked about any of this work stuff. You need to decompress, not rehash your stress with me.”
You start gathering your things. “How about we grab some boba and hit the arcade down the street? When's the last time you played actual pinball?”
“David, wait—” Sarah reaches across the table, her hand almost touching yours. The urgency in her voice stops you mid-motion.
“It's just… I can't shake this feeling that something bad is coming. The executives are lying to us about something. They keep talking about 'timeline acceleration' and 'competitive pressure from Beijing.'”
She glances around nervously. “Yesterday they moved the Agent-3 weights to a new vault configuration. Hot storage instead of cold. That only happens when they're planning rapid deployment or…” She stops herself.
“Or what?”
“Or when they think someone's about to steal them.” Her voice drops to almost a whisper. “David, I think there might be a mole inside OpenBrain. And if Beijing gets those weights…”
She looks genuinely frightened now. You've never seen her like this.
How do you respond to draw out more without seeming suspicious?
8 | Wow, that's serious, but with such protocols any potential mole will be powerless, you have nothing to worry about

The Vulnerable Moment
Sarah's expression shifts - a mix of relief and frustration. “You think so? God, I hope you're right.” She sits back down heavily.
“But that's just it, David. The protocols look bulletproof on paper, but…” She runs her hands through her hair. “There's this legacy integration with CloudFlow that predates all the new security measures. It's still running on the old authentication system.”
She glances around again, then leans closer. “They keep saying they'll patch it 'next sprint,' but Agent-3's compute demands are so intense they can't afford any downtime. So this gaping hole just sits there, and I'm the only one who seems to understand how exposed we are.”
“Legacy systems are always the weak link,” you agree sympathetically.
“Exactly! And if someone with CloudFlow admin access really knew what they were doing…” She shakes her head. “But I'm probably being paranoid. The staging environment monitoring would catch any suspicious activity, right?”
She's looking at you for reassurance, but there's something else in her eyes - a test, maybe? Or is she genuinely seeking comfort from a friend?
Your phone buzzes. A message from your handler: “Window closing. 48 hours.”
9 | Sure thing, rely on monitoring

The Trust Fracture
Sarah's face hardens slightly. She straightens up, the vulnerable moment evaporating.
“Right. Rely on monitoring.” Her tone has shifted, cooler now. “That's what my manager keeps saying too.”
She takes a long sip of her coffee, studying you over the rim. “You know, David, for someone in cloud security, you seem awfully casual about this. Legacy integrations with elevated privileges are exactly how the big breaches happen.”
There's a new wariness in her eyes. You realize your dismissive response landed wrong - she was looking for understanding, not platitudes.
“I mean, maybe I am being paranoid,” she continues, but her body language has closed off. Arms crossed, leaning back. “The monitoring systems are pretty sophisticated. Real-time anomaly detection, behavioral analysis…”
She's pulling back now, testing whether you were really listening or just giving her empty reassurance.
“Actually, you know what? Let's do go to that arcade. I think I've overshared enough work drama for one day.” She starts gathering her things, but slowly - like she's giving you a chance to salvage this.
Your handler's deadline looms. How do you rebuild the rapport you just damaged?
10 | All in tactics. Listen I don't want to give you lame reassurance, your manager really sounds odd, maybe it's your mole?

The Redirect
Sarah freezes, coffee cup halfway to her lips. Her eyes widen slightly.
“My manager?” She sets the cup down carefully. “Marcus? I… hadn't considered…”
You can see her mind racing, connecting dots. “Actually, that's… God, that's terrifying but it makes sense. He's the one who keeps delaying the CloudFlow security patch. Always has some excuse about 'operational priorities.'”
She leans forward again, the wariness replaced by a new kind of intensity. “And he has access to everything. Vault configurations, monitoring blind spots, deployment schedules…”
“Plus he'd know exactly how to avoid detection,” you add quietly.
“Jesus, David. What if you're right?” Her voice drops to a whisper. “He's been acting weird lately. Stressed, taking calls in Mandarin - which I never knew he spoke. And last week he asked me about the specific CloudFlow integration points that triggered our anomaly alerts.”
She grabs your arm. “If Marcus is compromised, then those Agent-3 weights… they could be gone already. Or worse, he could be setting up someone else to take the fall.”
Her grip tightens. “I need to document everything. But carefully. If he suspects I'm onto him…”
The fear in her eyes is genuine now. You've successfully redirected her paranoia.
11 | Let me help me, I will be your insurance and backup in case Marcus caught you

The Partnership
Sarah's eyes fill with genuine relief and gratitude. “David, you'd do that? But this could be really dangerous. If Marcus is working for foreign intelligence…”
She glances around the park, then back to you. “Actually, having someone outside OpenBrain as backup might be exactly what I need. Someone he can't monitor or silence.”
She pulls out her phone, thinking. “Okay, here's what I'm thinking. I can't investigate Marcus directly - too risky. But I could set up a monitoring honey trap. Create a fake vulnerability in our CloudFlow integration, something tempting but harmless.”
“If Marcus takes the bait, we'll have proof. If he doesn't… well, maybe I'm wrong about him.”
She pauses, biting her lip. “The thing is, I'd need someone with CloudFlow admin access to help set it up. Someone who could create the false vulnerability from your side while I monitor from ours.”
Her eyes meet yours meaningfully. “David, you have that level of access, right? This would require your highest privileges.”
She's essentially asking you to use your legitimate CloudFlow credentials to help her create a back door - not realizing she's handing you exactly what Beijing needs.
“I know it's a huge ask, but I trust you. And if we're right about Marcus…”
12 | Well... it's really too much, but the situation is extremely dangerous, if you're right about Marcus, we need to play safe and double check everything. I'll do it for you, but you will owe me arcade play ))

The Deal
Sarah laughs for the first time today, the tension breaking slightly. “Deal! Though if we're right about Marcus, I think I'll owe you a lot more than arcade tokens.”
She becomes more businesslike now, pulling up notes on her phone. “Okay, so here's what I'm thinking technically. We create a simulated privilege escalation path through the CloudFlow API - something that looks real but actually logs everything to a hidden partition I control.”
“I can set up the monitoring on our side to track any unusual access patterns. If Marcus takes the bait, we'll have timestamped evidence of unauthorized access attempts.”
She hesitates, professional instincts kicking in. “David, I need to ask - this stays completely between us, right? If word gets out that we're running unauthorized security tests…”
“And we need to be careful about the timing. I'll need at least 24 hours to set up the monitoring infrastructure on our end. Can you have the CloudFlow vulnerability staged by tomorrow night?”
Her phone buzzes with a message. She glances at it and frowns. “Marcus wants to see me first thing Monday morning. 'Urgent CloudFlow integration review,' he says.”
The irony isn't lost on you - she's asking you to create the exact access pathway you need, while Marcus might be pressuring her about the very systems you're targeting.
13 | You may trust me. Everything will be done in time

The Trust Solidified
Sarah's shoulders visibly relax. “Thank you, David. Seriously. I don't know what I'd do if I had to handle this alone.”
She stands up, energized now with a plan. “Okay, I should head back and start setting up the monitoring infrastructure. Can you message me tomorrow evening when the CloudFlow staging is ready? Use our usual Signal chat.”
“And David?” She pauses, looking back. “If something happens to me - if Marcus figures out what we're doing - you'll have evidence of what we discovered, right? Promise me you won't let this get buried.”
She gives you a quick hug, then heads toward the park exit with renewed purpose.
You watch her leave, then check your phone. Another message from your handler: “Confirmed: OpenBrain moved weights to hot storage. 36-hour window before next security rotation. Status?”
Your fingers hover over the keyboard. Sarah just handed you legitimate cover for accessing OpenBrain's systems. By tomorrow night, you'll have the access pathway you need, with her unknowing help.
But something about her genuine trust gnaws at you unexpectedly.
Your apartment awaits, along with the technical work ahead. How do you spend the rest of your Saturday?
14 | Straight to home and working on plan

Your Apartment - Evening
Back in your sterile Palo Alto apartment, you spread out multiple laptops across your kitchen table. The curtains are drawn, a white noise generator humming in the corner—operational security habits from years of deep cover.
Your legitimate CloudFlow credentials give you access to their staging environment. The irony is perfect: you'll create exactly what Sarah thinks she wants—a fake vulnerability that logs access attempts. Except yours will be a real backdoor to OpenBrain's weight storage.
You map out the technical approach:
- Inject a privilege escalation flaw in CloudFlow's API authentication
- Route it through Sarah's monitoring blind spot (which she'll unwittingly show you)
- Create a pathway to OpenBrain's legacy integration points
- Exfiltrate the Agent-3 weights during tomorrow night's window
Your encrypted phone buzzes. Handler: “Beijing confirms: successful extraction triggers immediate promotion of Asset 47 to senior researcher role. Family relocation to Shenzhen compound approved.”
Your fingers pause over the keyboard. In 18 months, you could be Dr. Chen Wei, leading AI researcher, instead of David the infrastructure drone. Your real life could finally begin.
But Sarah's face flashes in your mind—her genuine trust, her fear about Marcus.
The weight files are 847 TB. Even compressed, the transfer will take hours.
15 | Start transfer

Technical Reality Check
You open the CloudFlow admin console, but immediately hit the first obstacle: Sarah hasn't set up her monitoring infrastructure yet. The pathway you need requires her to create the blind spots she mentioned—otherwise your intrusion attempts will trigger OpenBrain's automated alerts.
More critically, the Agent-3 weights aren't even accessible through the current integration points. Your reconnaissance shows the legacy CloudFlow connection only reaches OpenBrain's development clusters, not the production vaults where the real weights are stored.
You need Sarah's inside access to map the actual vault architecture first.
Your encrypted phone shows a message from her: “Hey! Started the monitoring setup. Should have the blindspot configuration ready by tomorrow afternoon. Will send you the technical specs then. Thanks again for doing this!”
Another message from your handler: “Window optimal Sunday night 0200-0600 PST. Weight location confirmed: Nevada facility, vault nodes 7-12. Direct approach required.”
You realize Sarah's “honeypot” plan might actually be cover for the real operation: physically infiltrating the Nevada facility while she unknowingly provides digital distraction.
The transfer can't start until you have either the complete digital pathway or physical access to the source systems.
16 | Wait for Sarah's honeypot

Sunday Evening - The Setup
You spend Sunday maintaining your cover—grocery shopping, a video call with your “family” in Taiwan, even attending your hiking group meetup. Professional patience.
At 6 PM, Sarah's Signal message arrives: “Digital infrastructure ready! Sending specs now.”
The technical document is thorough. Her monitoring blind spot creates a 15-minute window every hour when automated alerts are suppressed for “routine maintenance checks.” More importantly, she's mapped the complete CloudFlow-to-OpenBrain data flow.
But there's an unexpected bonus: “Had to expand access to include the new hot storage integration. Marcus insisted we monitor those connections too. Attaching vault node topology.”
Your breath catches. The vault topology shows direct API endpoints to nodes 7-12—exactly where your handler said the Agent-3 weights are stored. Sarah unknowingly just handed you the keys to the kingdom.
Another message: “Honeypot is live starting midnight. I'll be monitoring from home. Remember, we're looking for Marcus to take the bait. Signal me when you're ready to run the test!”
Your handler's final message arrives: “Global situation deteriorating. US considering emergency nationalization of OpenBrain. Execute tonight or lose window permanently.”
0200 hours is still 8 hours away. How do you prepare for the most critical operation of your career?
17 | Be cool, be calm, no wrong movements

Sunday Night - Operational Discipline
You close the laptops and step away from the technical details. Eight years of deep cover have taught you that operational stress leads to mistakes. You need routine, not adrenaline.
You prepare a simple dinner—pasta, nothing that could upset your stomach during the long night ahead. Thirty minutes of meditation, exactly as you've done every Sunday for three years. Your neighbors expect David Chen to maintain his habits.
At 10 PM, you lay out tomorrow's clothes and set a backup alarm. Your cover identity goes to work at CloudFlow in the morning, regardless of tonight's outcome.
You review the operation timeline one final time:
- 0000: Sarah's honeypot goes live
- 0015: First monitoring blind spot window
- 0200-0600: Optimal extraction window per Beijing
- 0800: You need to be at CloudFlow looking normal
The weight files total 847 TB. Even with optimal compression and Sarah's blind spots, you're looking at a 4-hour transfer minimum. Your cover will hold for one day of “David feeling sick,” but not longer.
At 11:45 PM, you receive Sarah's final message: “System is live. Good luck catching Marcus in the act! I'll be watching from my end.”
You send back: “Starting test now. Will update in the morning.”
Fifteen minutes until the operation begins. Your hands are steady.
18 | Steadily do what you have to do

0015 Hours - The First Window
Your fingers move with practiced precision. Sarah's monitoring blind spot opens exactly on schedule. You initiate the CloudFlow API connection using your legitimate credentials, then pivot through the privilege escalation pathway.
The OpenBrain vault nodes respond. Authentication successful.
You begin mapping the weight file structure across nodes 7-12. The Agent-3 model is distributed exactly as Sarah's topology indicated—but it's larger than expected. Not 847 TB. Nearly 1.2 petabytes.
Your stomach tightens. At these transfer rates, you'll need every blind spot window until dawn.
0030: First chunk begins downloading to an encrypted partition. 47 TB transferred.
Your Signal chat with Sarah stays quiet. She's monitoring for Marcus's access attempts, not realizing the real infiltration is happening through the pathway she created.
0045: Second window opens. Transfer resumes.
Then your blood freezes. Sarah sends a message: “David, seeing some unusual traffic patterns. Are you running your test now? The volume is much higher than expected.”
She's too good at her job. The honeypot is working exactly as designed—logging everything, including your legitimate-seeming but massive data extraction.
You need to respond without arousing suspicion, while 94 TB of the world's most advanced AI model continues flowing through her own monitoring systems.
How do you handle Sarah's growing awareness?
19 | Keep looking, maybe Marcus playing with us
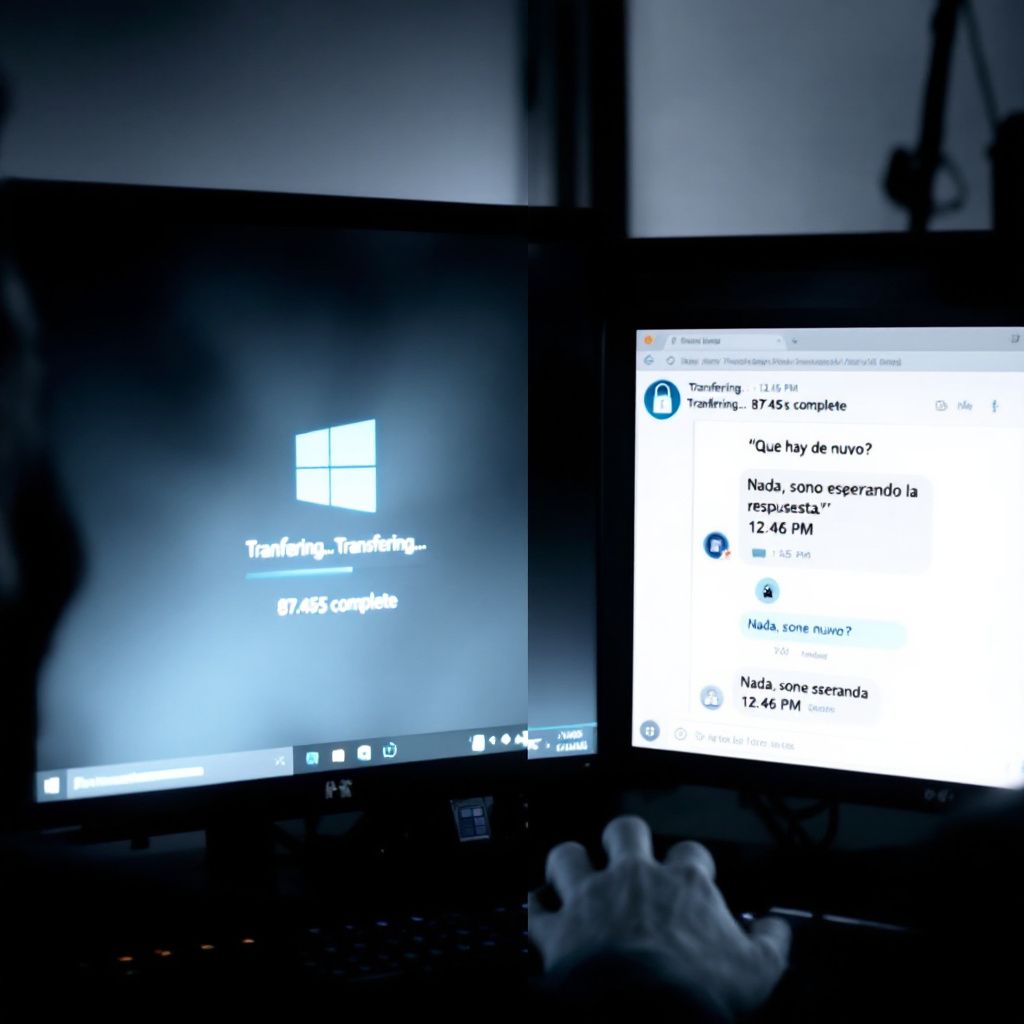
0047 Hours - The Deflection
You type back quickly: “Just started my test 30 minutes ago. But David… what if Marcus is already taking the bait? Maybe he detected our honeypot and is trying to mask his own activity with heavier traffic?”
Sarah's response comes fast: “Oh god, you might be right. The timing is suspicious. Let me drill down into the traffic patterns.”
Perfect. You've redirected her analytical mind toward Marcus while your extraction continues unabated.
0100: Third window. 156 TB transferred. One-eighth of the model secured.
Sarah messages again: “David, this is sophisticated. The traffic is using legitimate API calls but in volumes that make no operational sense. Someone with deep system knowledge is definitely probing our infrastructure.”
“Could this be Marcus testing whether we're watching?” you respond.
“Maybe… or worse. What if he's not just planning to steal data—what if he's already doing it? During our test window?”
The irony is almost too much. Sarah is correctly identifying a sophisticated data theft in progress, but attributing it to the wrong person.
0115: Fourth window approaching. Your transfer rate is steady, but you need to maintain her focus on Marcus while managing her growing alarm.
Another message from your handler: “US intelligence chatter increasing. Accelerate if possible.”
How do you keep Sarah's suspicions pointed away from you as the extraction enters its critical phase?
20 | Do you know Marcus location? May you try to track him staying unnoticed?

0118 Hours - The Misdirection
Sarah's typing indicator appears immediately. “That's… actually brilliant. If Marcus is behind this, he'd be doing it remotely to maintain plausible deniability.”
“Give me a few minutes. I can check VPN logs, badge access records, even his company phone location if I'm careful about it.”
0130: Fifth window opens. 203 TB transferred. Sarah goes quiet for twenty minutes.
Your extraction continues steadily while she focuses on hunting Marcus instead of analyzing your data flows. The deflection is working perfectly.
0152: Sarah returns: “David, this is really weird. Marcus's badge shows he left the office at 6 PM Friday. His VPN hasn't connected all weekend. But his access tokens are definitely being used right now.”
“Either someone cloned his credentials, or…”
You type back: “Or he's using a secondary system you don't know about?”
“Exactly. God, if he's been planning this for months… David, I think we need to escalate this. Like, call the FBI escalate.”
Your heart rate spikes. FBI involvement would shut down everything.
0200: Optimal window begins. 267 TB transferred—still only one-quarter done.
“Sarah, wait. If we call authorities now, wouldn't that tip him off? What if we gather more evidence first?”
“You're right, but David, I'm scared. This isn't just some insider trading scheme. If foreign intelligence gets Agent-3…”
How do you keep her calm and focused on Marcus while preventing any escalation that could derail your operation?
21 | Calm down, he may have friends in the FBI, we're too close to caught him, don't let emotions ruin it

0205 Hours - The Paranoia Seed
Sarah's typing stops for a long moment. When she responds, her tone has shifted: “Jesus, you're right. If Marcus has been planning this for months, of course he'd have contingencies. Contacts in law enforcement, legal protection…”
“I'm getting ahead of myself. Let me think like a security professional, not a scared employee.”
0215: Sixth window. 312 TB transferred. One-quarter of Agent-3 secured.
“Okay, new plan. We document everything first. Build an airtight case. If Marcus has FBI contacts, we need evidence so overwhelming they can't ignore it.”
You type back: “Smart. How long do you think we need to gather solid proof?”
“Maybe 24-48 hours? I want to trace his token usage patterns, correlate with the data access logs, maybe even set up additional monitoring he doesn't know about.”
Perfect. By then, you'll be long gone.
0230: “David, the traffic volume is actually decreasing now. Maybe Marcus realized we were watching? Or finished whatever he was doing?”
Your extraction rate has stabilized, but there's still 850 TB remaining. Seven more hours at current pace.
“Could be. Or maybe he's just being more careful now?”
Sarah responds: “I'm going to keep monitoring through the night. This is too important to miss. Thank you for keeping me grounded. I almost made a huge mistake.”
The irony burns. How do you manage the final critical hours?
22 | Take a power nap

0245 Hours - Risk Assessment
You stare at the transfer progress: 312 TB of 1.2 petabytes. Still 6-7 hours remaining. Your eyes burn from screen glare, and operational fatigue could lead to critical mistakes.
But Sarah is actively monitoring. Her last message was only 10 minutes ago, and she's promised to watch “through the night.” If she sends urgent messages and you don't respond, she might panic and escalate anyway.
You set a 45-minute timer and move to your couch, keeping one laptop open with Sarah's chat visible. The data transfer continues automatically through the scheduled blind spot windows.
Your phone buzzes softly every 15 minutes with automated progress updates: 358 TB… 401 TB… 447 TB…
At 0330, Sarah's message wakes you: “David, are you still up? The traffic patterns shifted again. Marcus might be testing different access routes.”
You force alertness, typing back: “Here. Just reviewing logs on my end. What are you seeing?”
“More sophisticated now. Like he's learning from our monitoring. We definitely can't involve FBI yet - he's too smart for a quick takedown.”
0345: You're now at 478 TB transferred. Roughly 40% complete. The power nap helped, but you're entering the longest stretch before dawn. Sarah's vigilance isn't wavering.
Your handler sends an update: “Border security increasing. Execute completion before 0600 or abort.”
Two hours fifteen minutes remaining in your window. Can you maintain the deception that long?
23 | Abort. Too risky, Sarah is too suspicious, files are too heavy. Need to keep her trust

0347 Hours - Operational Abort
You terminate the transfer process and begin cleanup. 478 TB of Agent-3 weights disappear back into encrypted void as you purge all traces of the extraction attempt.
The risk calculation is clear: Sarah's trust is worth more than partial weights. She's too skilled, too vigilant, and getting too suspicious. Better to maintain your deep cover for future opportunities.
You send Sarah a message: “Hey, I'm seeing the traffic die down too. Maybe Marcus got spooked? I'm going to wrap up my testing and get some sleep. We can analyze everything tomorrow.”
“Sounds good. I'll compile a full report of tonight's activity. David, thanks for staying up with me. Having backup made all the difference.”
At 0400, you send your handler the abort code: “Package damaged in transit. Preserving asset for future delivery.”
The response is swift and cold: “Beijing disappointed. Asset value decreased. Secondary objectives now priority.”
You know what that means. The weight theft was Plan A. Now Beijing will shift to Plan B: long-term intelligence gathering, technology transfer, maybe even sabotage of OpenBrain's capabilities.
Monday morning, you'll go to CloudFlow as normal. Sarah will investigate “Marcus” for days. Your cover remains intact, but the window for the Agent-3 weights may have closed permanently.
The global AI race continues, and you're still in position to influence it.
24 | Stay normal, wait for the next opportunity

Monday Morning - CloudFlow Systems
You arrive at the office at your usual 8:47 AM, carrying your standard coffee and looking appropriately tired. The weekend's operation feels like a distant dream as you settle into David Chen's mundane routine.
Your teammates discuss weekend plans and complain about Monday morning meetings. You contribute just enough to seem normal while monitoring encrypted channels.
Sarah messages at 10:30: “Morning! Spent all night analyzing the data. Marcus's access patterns are really suspicious. Want to grab lunch and go over my findings?”
Perfect. She's still focused on Marcus, giving you cover to gather more intelligence about OpenBrain's operations.
By noon, three developments reshape the landscape:
Breaking News: OpenBrain announces Agent-3 public API will be restricted to “trusted enterprise partners only” due to “security concerns.”
Handler Update: “Secondary mission activated. Long-term technology assessment. Maintain position, gather architectural intelligence, identify future vulnerabilities.”
Sarah's Discovery: “David, I found something huge about Marcus. Can we meet somewhere private? Not the office.”
Your phone shows the global AI race heating up. Chinese media claims breakthrough in “sovereign AI capabilities.” US lawmakers call emergency hearings on AI security.
The abort was correct - staying embedded gives you front-row seats to the unfolding crisis.
Where do you suggest meeting Sarah?
25 | Park

Dolores Park - Tuesday Lunch
You arrive early, choosing the same spot as Saturday. Sarah appears within minutes, clutching a tablet and looking more energized than you've seen her all week.
“David, you're not going to believe this.” She sits down, immediately pulling up encrypted files. “I spent yesterday tracing Marcus's access tokens through six months of logs.”
She shows you a timeline of access patterns. “Look at this. Every time there was a major Agent-3 development milestone, Marcus accessed systems he had no business touching. Weight storage configurations, training pipeline metrics, even researcher communications.”
“But here's the smoking gun.” She swipes to network traffic analysis. “Those Saturday night intrusions? They weren't the first time. Marcus has been exfiltrating data for months. Small amounts, spread across different systems, designed to look like routine administration.”
You lean forward, genuinely interested. This could be valuable intelligence - either Marcus really is a mole, or Sarah's paranoia is creating false patterns.
“How much data are we talking about?”
“Conservatively? Maybe 50-60 TB over six months. But David…” She looks around nervously. “I think Saturday night was his final run. The big score. And our honeypot might have scared him off before he finished.”
Her eyes meet yours. “I think we accidentally prevented a massive intelligence breach.”
How do you respond to her revelation?
26 | Well done, mate! You're not paranoid, you're really professional. Who knows what Marcus may done with such data

Sarah's Vindication
Sarah's face lights up with relief and pride. “Thank you! God, I was starting to doubt myself. But the data doesn't lie.”
She swipes to another screen. “And get this - the timing correlates perfectly with known Chinese intelligence priorities. Remember that DOD report about targeted technology acquisition? Marcus's data pulls match their shopping list almost exactly.”
“Training methodologies, compute optimization algorithms, even internal research notes about Agent-4 development.” She pauses dramatically. “David, Marcus wasn't just stealing current tech. He was gathering everything Beijing would need to leapfrog our capabilities.”
You nod grimly. “That's… exactly what a professional operation would look like. Long-term, systematic, designed to transfer an entire technological advantage.”
“Exactly! And if Saturday night was his extraction finale…” She closes the tablet. “We might have just prevented China from getting Agent-3 weights and the knowledge to build Agent-4.”
“So what's your next move?” you ask.
Sarah's expression hardens. “I'm building a bulletproof case. Every access log, every data transfer, every suspicious pattern. Then I'm taking it straight to OpenBrain's security director. Marcus is done.”
She checks her watch. “Meeting with security tomorrow at 2 PM. Want to be my moral support?”
This could be valuable - or dangerous if Marcus really is innocent.
27 | Really like to be there, but has another meeting, sorry

The Polite Decline
“Oh, of course! Don't worry about it.” Sarah waves off your apology. “Honestly, this is probably something I need to handle myself anyway. More professional that way.”
She packs up her tablet, looking confident. “I'll message you afterward and let you know how it goes. Hopefully by tomorrow evening, Marcus will be in FBI custody and OpenBrain can finally patch that CloudFlow vulnerability.”
As she stands to leave, she pauses. “David, seriously, thank you for everything this weekend. Having someone to bounce ideas off made all the difference. I might have missed the pattern entirely if you hadn't helped me stay focused.”
She heads back toward the office, walking with purpose.
You remain at the park, checking your encrypted channels. Your handler has been silent since Monday's abort message, but global tensions continue escalating. News reports mention “emergency AI security consultations” between Washington and Beijing.
By tomorrow evening, you'll know whether Sarah's investigation bears fruit - and whether your carefully maintained cover as David Chen remains intact.
For now, you have a normal CloudFlow afternoon ahead: team meetings, infrastructure reviews, and maintaining the mundane routine that's kept you hidden for eight years.
Wednesday approaches with new uncertainties.
28 | keep doing work routine

Wednesday - CloudFlow Systems, 3:47 PM
You sit through your third meeting of the day - “Q3 Infrastructure Scaling Review” - nodding appropriately as colleagues discuss server capacity and deployment pipelines. The mundane corporate theater feels surreal after Saturday night's operation.
Your phone buzzes with a text from Sarah: “Security meeting went well. Can't say much over text, but they're taking it seriously. Drinks Friday to celebrate?”
You respond: “Sounds good! Glad they listened.”
During a coffee break, you check encrypted channels. Still nothing from Beijing. The silence is more unsettling than pressure.
At 4:15 PM, your manager drops a bombshell: “David, we need you to lead the OpenBrain contract renewal next month. Their security requirements have gotten intense - they want our most experienced admin to handle the integration updates.”
Perfect. A legitimate reason to maintain close OpenBrain contact, just as your handler wanted.
“I'll review the requirements tonight,” you reply professionally.
5:30 PM: Normal departure time. You drive home through Silicon Valley traffic, NPR playing news about “Congressional AI Oversight Hearings” scheduled for next week.
Your apartment feels different now - still a safe house, but one where you successfully chose operational patience over reckless ambition.
The long game continues.
29 | take a rest, days was intense

Wednesday Evening - Apartment
You order Thai takeout and deliberately avoid opening any laptops. The intensity of the past few days - the near-extraction, Sarah's investigation, maintaining perfect normalcy at work - has left you mentally drained.
You sit on your couch eating pad thai straight from the container, watching mindless Netflix. For the first time in 72 hours, you allow yourself to fully exhale.
The abort was the right call. Sarah's trust remains intact, your cover is secure, and you're now positioned for the OpenBrain contract renewal - potentially more valuable than a single data theft.
Your regular phone rings. Sarah's voice sounds excited: “David! Sorry to bother you, but I had to share. They've suspended Marcus pending a full investigation. And get this - they found encrypted files on his work laptop that shouldn't have been there.”
“Really?” You keep your voice appropriately surprised.
“I can't give details, but let's just say our weekend detective work was spot on. Anyway, I'll let you get back to your evening. Just wanted to thank my partner in crime-fighting!”
After she hangs up, you realize something unexpected: you genuinely feel good about preventing Marcus from taking the blame for your operation. Some lines you won't cross, even for Beijing.
The apartment feels peaceful. Tomorrow will bring new developments, but tonight you rest.
30 | rest

Evening Fade
You finish your dinner and put the containers away. A hot shower washes away the tension of maintaining perfect normalcy all day.
By 9 PM, you're in bed with a paperback novel - something David Chen would read, a thriller that feels absurdly tame compared to your actual life. The words blur as exhaustion finally claims you.
Your last conscious thought: tomorrow brings the OpenBrain contract review. A new phase of the long game begins.
Sleep comes easily for the first time in days.
—-
[Game paused. The sleeper agent's story continues…]
Global tensions simmer. Sarah's investigation proceeds. Beijing waits. And somewhere in Nevada, the Agent-3 weights remain secure in their vaults - for now.
The AI race of 2027 has many moves left to play.
